Where to find TCS process for business continuity management? This crucial question drives organizations seeking to understand Tata Consultancy Services’ (TCS) robust approach to mitigating disruptions. This guide delves into the core components of TCS’s Business Continuity Management (BCM) framework, exploring its methodologies, documentation, and technological underpinnings. We’ll examine how TCS integrates risk assessment, business impact analysis, and recovery strategies, comparing its practices against industry standards like ISO 22301. Understanding TCS’s BCM is vital for both TCS clients and those seeking best-practice examples in the field.
We’ll navigate the official TCS resources, highlighting where to locate publicly available information and outlining the structure of internal documentation. We’ll also explore the practical application of TCS’s BCM through a hypothetical scenario, illustrating their response plan and recovery procedures. By the end, you’ll possess a clear understanding of TCS’s commitment to business continuity and how its processes ensure operational resilience.
TCS Business Continuity Management (BCM) Overview

TCS’s Business Continuity Management (BCM) framework is a comprehensive system designed to ensure the organization’s continued operation during disruptive events. It encompasses a proactive approach to risk identification, mitigation, and recovery, aiming to minimize the impact of incidents on business operations and maintain service delivery to clients. This framework is underpinned by a robust set of principles and methodologies, constantly evolving to meet the dynamic challenges of the modern business landscape.
TCS’s BCM framework is built on several core components. These components work in synergy to provide a holistic approach to business continuity. The framework is not static; it is regularly reviewed and updated to reflect changes in the threat landscape and business operations.
Core Components of TCS’s BCM Framework
The TCS BCM framework comprises several key components, including business impact analysis (BIA), risk assessment, business continuity plan (BCP) development, testing and exercises, and ongoing maintenance and improvement. The BIA identifies critical business functions and their dependencies, quantifying potential losses from disruptions. Risk assessment evaluates the likelihood and impact of various threats, informing the development of mitigation strategies. The BCP Artikels procedures for resuming operations after a disruptive event. Regular testing and exercises validate the effectiveness of the BCP, ensuring readiness for real-world scenarios. Continuous monitoring and improvement ensure the plan remains relevant and effective.
Key Principles Guiding TCS’s Approach to Business Continuity
TCS’s BCM approach is guided by several key principles. These principles emphasize proactive risk management, collaboration, and a commitment to continuous improvement. A core principle is the prioritization of client service continuity. The framework also emphasizes a holistic approach, integrating BCM into all aspects of business operations. This integrated approach ensures that business continuity is not a standalone function but an integral part of the organization’s overall risk management strategy. Furthermore, a commitment to transparency and communication is crucial, ensuring all stakeholders are informed and engaged throughout the process.
TCS BCM Methodologies and Best Practices
TCS employs a variety of methodologies and best practices in its BCM approach. These include using industry-standard frameworks like ISO 22301, incorporating IT disaster recovery planning, and leveraging technology to enhance resilience. The company emphasizes a risk-based approach, prioritizing resources to mitigate the most significant threats. Regular training and awareness programs ensure that employees understand their roles and responsibilities in the event of a disruption. Post-incident reviews are conducted to identify areas for improvement and refine the BCM framework, ensuring continuous learning and adaptation. These methodologies and best practices are regularly reviewed and updated to reflect changes in the threat landscape and best practices within the industry. The aim is to maintain a highly resilient and adaptable organization capable of withstanding various disruptions.
Locating TCS BCM Documentation and Resources
Accessing comprehensive information on TCS’s Business Continuity Management (BCM) processes might require navigating internal TCS portals and resources. Publicly available information is generally limited to high-level overviews and marketing materials, rather than detailed procedural documentation. This is standard practice for many large organizations to protect sensitive operational information.
Publicly available information focuses on TCS’s BCM capabilities and its commitment to business resilience, rather than specific internal procedures. This approach allows TCS to showcase its expertise while maintaining the confidentiality of its proprietary methodologies.
TCS Websites and Portals with BCM Information
Finding specific, publicly accessible documents detailing TCS’s internal BCM processes is unlikely. However, TCS’s main website and potentially industry-specific pages might contain general information on their BCM approach, highlighting their services and capabilities in this area. These sections would likely focus on the value proposition to clients, emphasizing TCS’s experience and expertise in helping businesses develop and implement robust BCM plans. Searching the TCS website using s like “business continuity,” “disaster recovery,” and “resilience” might yield relevant, albeit high-level, information.
Examples of TCS BCM White Papers and Case Studies
While direct links to TCS white papers or case studies specifically focused on their *internal* BCM processes are not readily available publicly, we can infer the likely content of such documents. A typical white paper might detail TCS’s BCM framework, methodologies, and technologies used. It could include examples of successful BCM implementations for clients across various industries, showcasing their approach to risk assessment, business impact analysis, recovery strategies, and testing procedures. Case studies would likely focus on specific client engagements, illustrating how TCS helped organizations improve their business resilience through tailored BCM solutions. These documents would likely emphasize the measurable benefits achieved, such as reduced downtime, improved recovery time objectives (RTOs), and enhanced business continuity.
Structure of TCS Internal BCM Documentation
TCS’s internal BCM documentation would likely follow a standardized structure, common to large organizations. This would involve a hierarchical organization, with overarching policies and procedures at the top, followed by more detailed plans and procedures for specific business units or functions. The documentation might include:
- BCM Policy: A high-level document outlining TCS’s overall commitment to BCM and establishing the framework for all related activities.
- Business Impact Analysis (BIA): Documents identifying critical business functions, their dependencies, and potential impact of disruptions.
- Recovery Strategies: Detailed plans for restoring critical business functions in the event of a disruption.
- Testing and Exercises: Documentation outlining the frequency and types of BCM tests and exercises conducted to validate the effectiveness of plans.
- Communication Plans: Procedures for communicating with stakeholders during and after a disruption.
- Roles and Responsibilities: Clearly defined roles and responsibilities for individuals and teams involved in BCM.
This structure ensures a consistent and comprehensive approach to managing business continuity across the organization. The specific details within each document would vary based on the specific business unit or function. Access to this internal documentation is restricted to authorized personnel within TCS.
Understanding TCS BCM Processes
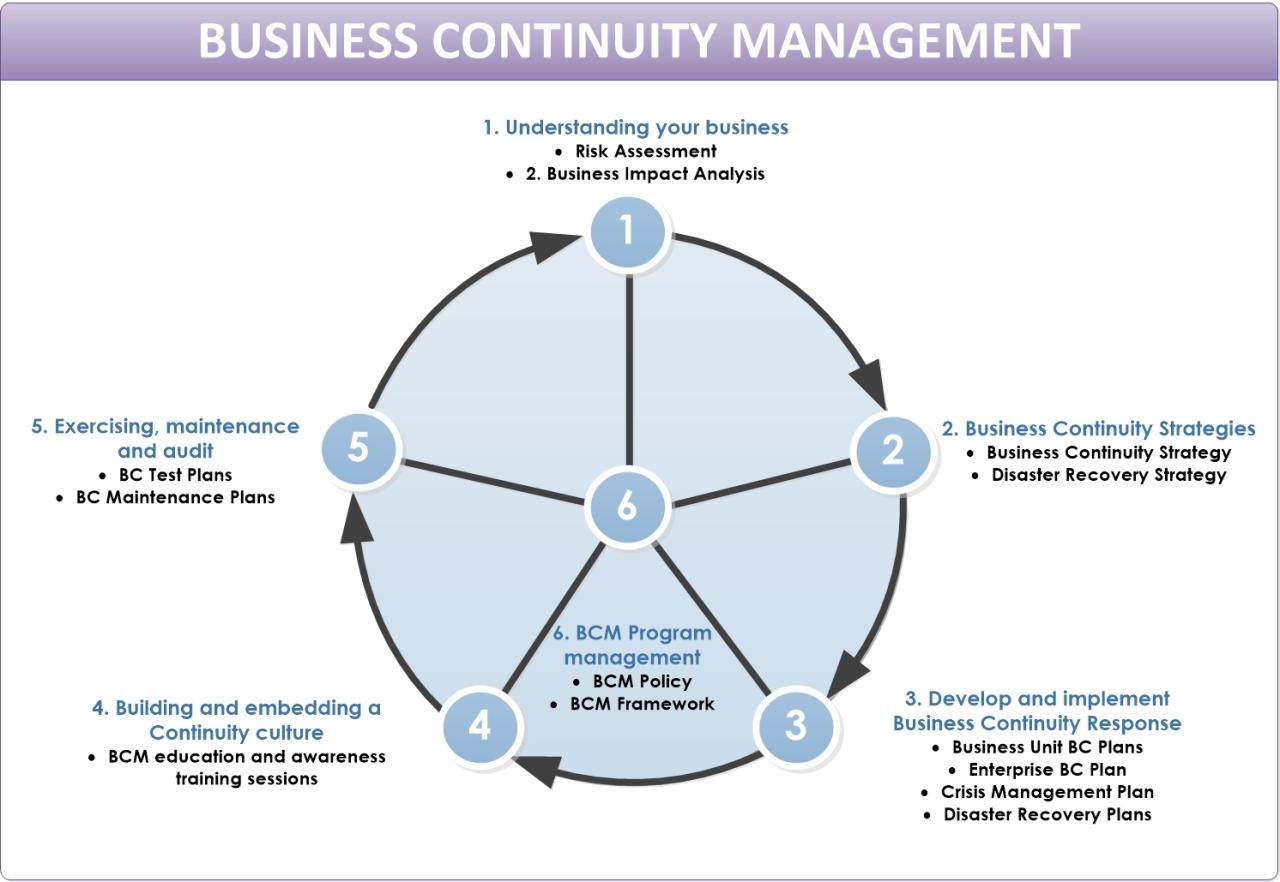
The TCS Business Continuity Management (BCM) process is a structured approach to identifying, assessing, mitigating, and recovering from disruptive events that could impact business operations. It’s a cyclical process, constantly reviewed and improved to ensure its effectiveness in a dynamic environment. Understanding the various stages and methodologies employed is crucial to appreciating the robustness of TCS’s BCM framework.
TCS’s BCM lifecycle encompasses several key stages, each contributing to the overall resilience of the organization. These stages are interconnected and iterative, ensuring continuous improvement and adaptation to evolving threats and vulnerabilities.
Stages in the TCS BCM Lifecycle
The TCS BCM lifecycle is typically represented as a continuous loop, not a linear progression. The key stages include Business Impact Analysis (BIA), Risk Assessment, Strategy Development, Plan Development and Testing, Implementation and Maintenance, and finally, Recovery and Review. Each stage involves detailed documentation and rigorous review processes. For example, the BIA process might involve surveys, interviews, and workshops with various business units to understand critical functions and their dependencies. The findings are then used to inform the risk assessment, strategy, and plan development phases.
Risk Assessment and Mitigation Strategies at TCS
TCS employs a comprehensive risk assessment methodology to identify potential threats and vulnerabilities to its business operations. This involves considering a wide range of factors, including natural disasters, cyberattacks, pandemics, and supply chain disruptions. Qualitative and quantitative methods are used to evaluate the likelihood and potential impact of each risk. For example, a quantitative risk assessment might involve assigning probability scores and impact levels to different threats, while a qualitative assessment would focus on expert opinions and scenario planning.
Once risks are identified and assessed, TCS develops and implements mitigation strategies to reduce their likelihood and impact. These strategies may include implementing robust security measures, developing disaster recovery plans, establishing redundant systems, and investing in business continuity training. A specific example might be the implementation of multi-site data centers to mitigate the risk of data loss due to a localized disaster. The selection of mitigation strategies considers cost-benefit analysis and the overall risk appetite of the organization.
Incorporating Business Impact Analysis (BIA) into TCS BCM Planning
Business Impact Analysis (BIA) is a critical component of TCS’s BCM planning process. A BIA systematically identifies and analyzes the potential consequences of disruptions to critical business functions. This process involves determining the maximum tolerable downtime (MTD) for each function and the recovery time objective (RTO) and recovery point objective (RPO) required to resume operations.
The MTD represents the maximum period a business function can be down before it causes unacceptable damage, while the RTO defines the timeframe within which a function must be restored, and the RPO specifies the acceptable data loss in case of a disruption.
The results of the BIA are used to prioritize resources and develop effective recovery strategies. For instance, a function with a short MTD and RTO would receive higher priority in the recovery plan than a function with longer acceptable downtime. The BIA ensures that the BCM plan focuses on the most critical business functions, optimizing resource allocation and ensuring business continuity during disruptive events. Regular updates and reviews of the BIA are essential to reflect changes in the business environment and evolving threats.
TCS BCM Implementation and Execution
Effective implementation and execution of TCS’s Business Continuity Management (BCM) plan are crucial for minimizing disruption and ensuring business resilience during crises. This involves clearly defined roles, robust communication protocols, and a well-rehearsed activation process. The success of the plan hinges on the preparedness and coordinated actions of various teams across the organization.
TCS’s BCM framework is structured to ensure a clear division of responsibilities and a streamlined response to incidents. This structure promotes accountability and efficient resource allocation during a crisis. Communication is paramount, and TCS utilizes multiple channels to maintain transparency and ensure timely information dissemination.
Roles and Responsibilities within TCS’s BCM Structure
The TCS BCM structure comprises several key roles, each with specific responsibilities. These roles work collaboratively to ensure the effective implementation and execution of the BCM plan. For example, the BCM Manager is responsible for the overall plan’s development and maintenance, while the Business Unit BCM Leads are responsible for implementing the plan within their respective units. Incident Management Teams are activated during events and are responsible for executing the plan’s actions. These teams include representatives from IT, communications, and relevant business units. Detailed roles and responsibilities are documented in internal TCS BCM documentation.
Communication Protocols and Escalation Procedures During Incidents
TCS utilizes a multi-layered communication strategy during incidents, ensuring that information flows efficiently to all stakeholders. This includes regular updates through various channels such as email, phone calls, and dedicated communication platforms. An escalation procedure is in place to ensure that critical incidents are promptly addressed by the appropriate management levels. This involves a defined escalation path, specifying who to contact and when, based on the severity and impact of the incident. For instance, minor incidents might be handled by the Business Unit BCM Lead, while major incidents might require escalation to senior management and the Crisis Management Team.
Activating and Managing TCS’s BCM Plan During a Crisis
The activation and management of TCS’s BCM plan during a crisis follow a structured process designed to ensure a coordinated and effective response. The steps involved are detailed below:
| Step Number | Step Description | Responsible Party | Timeline |
|---|---|---|---|
| 1 | Incident Identification and Assessment | Incident Management Team/Business Unit BCM Lead | Immediate |
| 2 | Incident Confirmation and Notification | BCM Manager/Incident Management Team | Within 1 hour |
| 3 | Activation of the BCM Plan | BCM Manager/Crisis Management Team | Within 2 hours |
| 4 | Implementation of Response Strategies | Relevant Teams (IT, Communications, Business Units) | Ongoing, based on the plan |
| 5 | Communication and Reporting | Communications Team/BCM Manager | Ongoing |
| 6 | Recovery and Restoration | Relevant Teams | Ongoing, until full recovery |
| 7 | Post-Incident Review and Lessons Learned | BCM Manager/Crisis Management Team | Within 2 weeks |
Comparison of TCS BCM with Industry Standards: Where To Find Tcs Process For Business Continuity Management
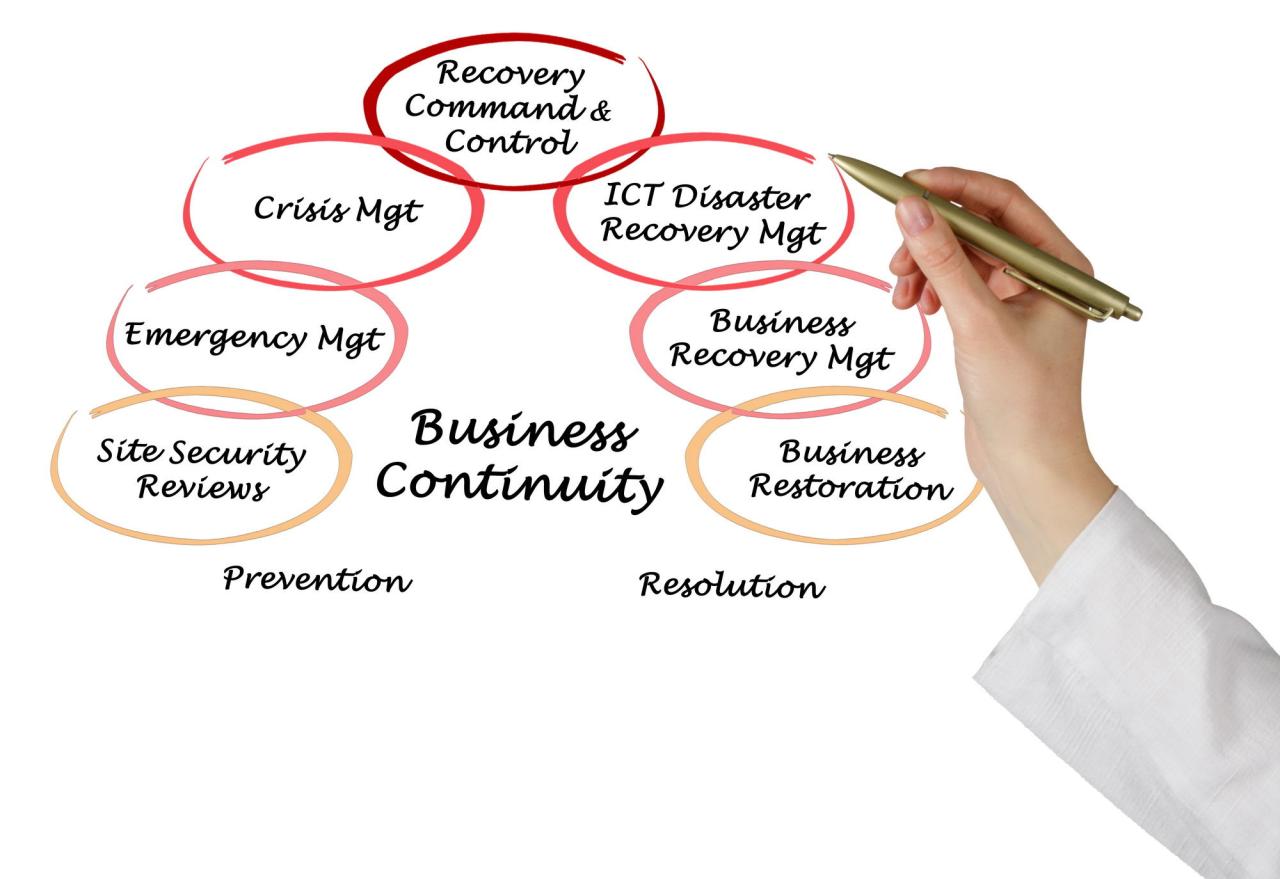
TCS’s Business Continuity Management (BCM) framework, while comprehensive, needs to be benchmarked against established industry standards to assess its effectiveness and identify areas for potential improvement. This comparison focuses on aligning TCS’s approach with the widely recognized ISO 22301 standard, highlighting both strengths and weaknesses.
A key aspect of this comparison involves examining the alignment between TCS’s internal BCM processes and the requirements Artikeld in ISO 22301. This international standard provides a framework for establishing, implementing, maintaining, and continually improving a documented BCM system. By comparing the two, we can pinpoint where TCS excels and where opportunities for enhancement exist.
Alignment with ISO 22301 Requirements
ISO 22301 mandates a structured approach to BCM, encompassing risk assessment, business impact analysis, recovery strategy development, and regular testing and review. TCS’s BCM framework likely incorporates many of these elements. However, a detailed comparison requires examining the specifics of TCS’s documented processes against each clause of ISO 22301. For example, the extent to which TCS’s risk assessments consider a wide range of potential disruptions (e.g., natural disasters, cyberattacks, pandemics) and the detail of its recovery strategies would be crucial points of comparison.
Areas Where TCS BCM Practices May Exceed Industry Best Practices
TCS, being a large global organization, likely possesses extensive resources and expertise in BCM. This could translate into practices that go beyond the minimum requirements of ISO 22301. For example, TCS might have implemented advanced technologies for monitoring and responding to incidents, or have a more sophisticated approach to supply chain resilience than what’s typically found in smaller organizations. A specific example could be the use of AI-driven predictive analytics to anticipate potential disruptions and proactively mitigate risks. This proactive approach would likely exceed the basic requirements of a typical ISO 22301 implementation.
Areas Where TCS BCM Practices May Fall Short of Industry Best Practices, Where to find tcs process for business continuity management
While TCS likely adheres to many industry best practices, potential areas for improvement could exist. One area could be the level of employee engagement and training in BCM procedures. A comprehensive BCM system relies on employee awareness and participation. Insufficient training or unclear communication could hinder the effectiveness of the framework. Another potential area is the regular testing and review of the BCM plan. Regular, realistic exercises are crucial to ensure the plan’s effectiveness and identify areas needing improvement. Insufficient testing could lead to delays and inefficiencies during an actual disruption.
Potential Areas for Improvement in TCS’s BCM Framework
Based on the comparison with ISO 22301 and other industry best practices, several potential areas for improvement could be identified. These might include enhancing the integration of BCM into the overall organizational risk management framework, improving communication and collaboration across different departments during a crisis, or strengthening the monitoring and evaluation of BCM effectiveness. Further analysis of TCS’s internal documentation and processes would be necessary to provide more specific recommendations.
Illustrative Scenario: A Major Cyberattack on TCS
A significant cyberattack targeting TCS’s global network infrastructure disrupts operations across multiple business units. The attack involves sophisticated ransomware, encrypting critical data and systems, including client project files, internal communication platforms, and financial databases. The attack also causes a widespread denial-of-service (DoS) event, rendering many online services inaccessible. This scenario highlights the potential impact of a severe cybersecurity incident on a large-scale global organization like TCS.
Incident Response and Activation of the BCM Plan
Upon detection of the cyberattack, TCS’s Security Operations Center (SOC) immediately activates its incident response plan, a key component of the broader BCM framework. This involves escalating the incident to the BCM team, who then initiate the pre-defined escalation procedures. The BCM team convenes an emergency response team composed of representatives from IT, security, communications, legal, and various business units. This team’s primary objective is to contain the attack, minimize further damage, and restore critical business functions as quickly as possible. The initial focus is on isolating affected systems to prevent further lateral movement of the ransomware.
Data Recovery and System Restoration
The recovery process utilizes TCS’s robust data backup and disaster recovery infrastructure. The team prioritizes the restoration of critical systems and data based on a pre-defined business impact analysis (BIA). This BIA, conducted as part of the BCM planning, identifies critical business functions and their recovery time objectives (RTOs) and recovery point objectives (RPOs). For example, systems supporting client projects with imminent deadlines are prioritized over less critical internal systems. The recovery leverages both on-site and off-site data backups, as well as redundant infrastructure in geographically diverse locations. The team employs specialized tools and techniques to decrypt the encrypted data, while ensuring data integrity and compliance with relevant regulations.
Communication and Stakeholder Management
Effective communication is crucial during the crisis. TCS establishes a dedicated communication channel to keep stakeholders informed. This includes clients, employees, investors, and regulatory bodies. Regular updates are provided on the situation, the recovery efforts, and the expected timeline for restoration. Transparency is prioritized to build trust and manage expectations. The communication strategy includes multiple channels, such as email, phone calls, dedicated web portals, and social media (where appropriate). The team proactively addresses concerns and misinformation to mitigate potential reputational damage.
Post-Incident Review and Lessons Learned
Following the successful restoration of services, a comprehensive post-incident review is conducted. This review analyzes the effectiveness of the response, identifies areas for improvement in the BCM plan, and highlights lessons learned. The findings inform updates to the BCM framework, security protocols, and incident response procedures. This iterative process ensures that TCS’s BCM capabilities continuously evolve and adapt to emerging threats and vulnerabilities. The review process also includes a detailed analysis of the financial impact of the incident and explores opportunities to improve resilience and reduce future risk.
Technological Aspects of TCS BCM
Technology plays a crucial role in supporting TCS’s Business Continuity Management (BCM) initiatives, enabling the organization to maintain operational resilience in the face of disruptions. TCS leverages a sophisticated technological infrastructure and a range of specialized tools to ensure business continuity and minimize the impact of unforeseen events. This involves robust disaster recovery mechanisms, comprehensive data protection strategies, and real-time monitoring capabilities.
TCS utilizes a multi-layered approach to technology-enabled BCM. This includes utilizing cloud-based infrastructure for increased flexibility and scalability, robust data backup and replication systems for data protection, and advanced security measures to prevent and mitigate cyber threats. The integration of these technologies allows for quick recovery and minimal downtime in the event of a disaster.
Cloud Computing and Infrastructure as a Service (IaaS)
TCS extensively uses cloud computing, particularly Infrastructure as a Service (IaaS), to enhance its BCM capabilities. This allows for rapid provisioning of resources in case of a disaster, enabling a swift recovery of critical systems and applications. The scalability of cloud-based solutions also allows TCS to adapt quickly to changing demands during a disruption. For example, if a data center experiences an outage, TCS can seamlessly shift workloads to a geographically dispersed cloud environment, minimizing service interruptions. The use of multiple cloud providers further enhances resilience and reduces single points of failure.
Data Backup and Replication Strategies
Data protection is paramount to TCS’s BCM strategy. The organization employs sophisticated data backup and replication techniques to ensure business-critical data is protected against loss or damage. This includes regular backups to multiple locations, both on-premises and in the cloud, utilizing technologies such as replication and mirroring. These strategies ensure data availability even in the event of a major disaster, such as a natural calamity or a cyberattack. Data encryption adds another layer of security, protecting sensitive information from unauthorized access.
Disaster Recovery (DR) and High Availability (HA) Solutions
TCS implements robust disaster recovery (DR) and high availability (HA) solutions to minimize downtime and ensure business continuity during disruptions. This includes geographically diverse data centers, failover mechanisms, and automated recovery processes. These systems are regularly tested through rigorous drills and simulations to validate their effectiveness and identify areas for improvement. The organization utilizes a combination of physical and virtual infrastructure to ensure redundancy and resilience. For instance, virtual machines can be rapidly spun up in a secondary data center in the event of a primary site failure, minimizing service interruption.
Security Information and Event Management (SIEM) Systems
TCS employs Security Information and Event Management (SIEM) systems to monitor its IT infrastructure for security threats and vulnerabilities. These systems collect and analyze security logs from various sources, providing real-time alerts and insights into potential security breaches. This proactive approach allows TCS to quickly identify and respond to threats, minimizing the impact on business operations. The data gathered by SIEM systems also helps in identifying patterns and trends, allowing TCS to improve its security posture and prevent future incidents.