Which of the following is a business critical integrity constraint? This question lies at the heart of robust database design and reliable business operations. Understanding business critical integrity constraints—those rules ensuring data accuracy and consistency vital to a company’s success—is paramount. This exploration delves into various constraint types, their implementation, and the potentially devastating consequences of neglecting them, offering practical strategies for maintaining data integrity and mitigating risk.
We’ll examine different types of constraints, such as referential integrity, check constraints, and unique constraints, illustrating how each safeguards specific aspects of data. Real-world examples and case studies will highlight the importance of proactive constraint implementation and the significant repercussions of failures. We’ll also cover best practices for managing changes to business rules and maintaining data integrity over time, even during migrations.
Defining Business Critical Integrity Constraints: Which Of The Following Is A Business Critical Integrity Constraint
Business critical integrity constraints are rules enforced within a database management system (DBMS) to maintain data accuracy and consistency, directly impacting the core functionality and operational success of a business. These constraints go beyond simple data validation; their violation can lead to significant financial losses, operational disruptions, or even legal repercussions. Understanding and correctly implementing these constraints is paramount for any organization relying on data-driven decision-making.
Database integrity constraints, in general, ensure data accuracy and consistency. However, business critical integrity constraints are a subset that directly affect the core business processes and operations. Their violation can cause immediate and substantial problems, unlike less critical constraints whose violations might only cause minor inconsistencies. For example, a constraint ensuring a customer’s address is valid is important, but a constraint ensuring that an order’s total price accurately reflects the sum of its items is business critical.
Real-World Scenarios Illustrating Business Critical Integrity Constraints
Several real-world scenarios highlight the importance of business-critical integrity constraints. Consider a banking system where a constraint ensures that the balance of an account never falls below zero. Violation of this constraint would lead to immediate financial problems and potentially legal issues. Similarly, in an e-commerce platform, a constraint guaranteeing that the quantity of a product in stock is never negative is crucial for preventing overselling and maintaining customer trust. In a hospital system, constraints ensuring patient data integrity, such as unique medical record numbers and accurate medication dosages, are vital for patient safety and legal compliance. These examples demonstrate how the failure to enforce business-critical integrity constraints can have severe consequences.
Classification of Business Critical Integrity Constraints
A useful classification system for business critical integrity constraints categorizes them based on the type of business rule they enforce. This can include:
- Financial Constraints: These constraints ensure the accuracy and consistency of financial data. Examples include preventing negative account balances, enforcing correct currency conversions, and maintaining audit trails for financial transactions.
- Inventory Constraints: These constraints manage inventory levels and prevent overselling or stockouts. Examples include checking available stock before processing orders and updating stock levels after each transaction.
- Operational Constraints: These constraints maintain the smooth functioning of core business processes. Examples include ensuring that orders are processed sequentially, that shipments are tracked accurately, and that deadlines are met.
- Legal and Regulatory Constraints: These constraints ensure compliance with relevant laws and regulations. Examples include enforcing age restrictions for certain products or services, and ensuring data privacy according to GDPR or CCPA.
Hypothetical Database Schema with Business Critical Integrity Constraints
Consider a simplified e-commerce database schema with tables for `Products`, `Orders`, and `OrderItems`.
| Table | Column | Data Type | Constraint |
|---|---|---|---|
| Products | ProductID | INT | PRIMARY KEY, UNIQUE |
| Products | ProductName | VARCHAR(255) | NOT NULL |
| Products | QuantityInStock | INT | CHECK (QuantityInStock >= 0) |
| Products | Price | DECIMAL(10,2) | NOT NULL, CHECK (Price > 0) |
| Orders | OrderID | INT | PRIMARY KEY, UNIQUE |
| Orders | CustomerID | INT | NOT NULL, FOREIGN KEY (Customers) |
| Orders | OrderDate | DATE | NOT NULL |
| Orders | TotalPrice | DECIMAL(10,2) | NOT NULL |
| OrderItems | OrderItemID | INT | PRIMARY KEY, UNIQUE |
| OrderItems | OrderID | INT | NOT NULL, FOREIGN KEY (Orders) |
| OrderItems | ProductID | INT | NOT NULL, FOREIGN KEY (Products) |
| OrderItems | Quantity | INT | NOT NULL, CHECK (Quantity > 0) |
| OrderItems | ItemPrice | DECIMAL(10,2) | NOT NULL, CHECK (ItemPrice > 0) |
This schema incorporates several business critical constraints: `QuantityInStock >= 0` in the `Products` table prevents negative stock levels; `Price > 0` ensures positive pricing; and a trigger could be implemented to ensure `TotalPrice` in the `Orders` table accurately reflects the sum of `ItemPrice * Quantity` from the `OrderItems` table. Foreign key constraints ensure referential integrity between tables. These constraints are all critical for the correct functioning of the e-commerce platform.
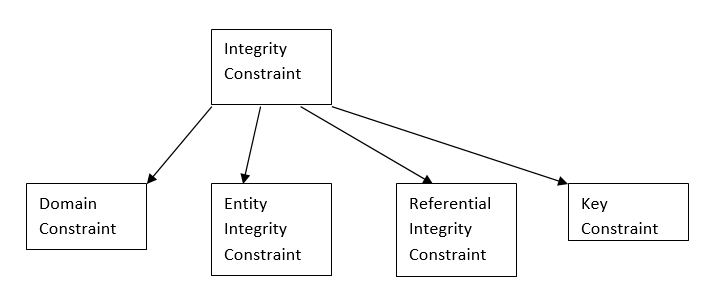
Types of Business Critical Integrity Constraints

Business critical integrity constraints are rules that ensure the accuracy, consistency, and reliability of data within a business system. Violating these constraints can lead to significant operational disruptions, financial losses, and reputational damage. Understanding the different types of these constraints and their potential impact is crucial for effective database design and operational risk management.
Entity Integrity
Entity integrity focuses on ensuring the uniqueness and validity of primary keys within each table. A primary key is a column or a set of columns that uniquely identifies each record in a table. It must contain unique values and cannot contain NULL values. Violating entity integrity, such as allowing duplicate primary key values, leads to data redundancy and inconsistencies, making it difficult to accurately identify and retrieve specific records. Enforcement mechanisms typically involve database triggers and constraints that prevent the insertion or update of records with non-unique or NULL primary keys.
Referential Integrity
Referential integrity maintains the consistency of relationships between tables by ensuring that foreign keys reference valid primary keys in related tables. A foreign key is a column in one table that references the primary key of another table, establishing a link between them. Violating referential integrity, such as attempting to create a record with a foreign key that does not exist in the referenced table, leads to orphaned records and data inconsistencies. Database systems typically enforce referential integrity using constraints that prevent such actions. Cascading updates and deletes are often implemented to manage the impact of changes on related records.
Domain Integrity
Domain integrity ensures that the values in a column adhere to a predefined data type and range. For example, a “price” column should only accept numeric values, and an “age” column should only accept positive integers. Violating domain integrity, such as entering text into a numeric field or an invalid date, can lead to data corruption and inaccurate reporting. Enforcement mechanisms rely on data type definitions within the database schema and input validation at the application level.
Unique Constraints
Unique constraints guarantee that all values in a specified column or set of columns are unique within a table. This is similar to the primary key constraint, but it doesn’t require the column to be a primary key. Unique constraints ensure data uniqueness and prevent duplicate entries. Violating a unique constraint, such as attempting to insert a duplicate value, will result in an error. Database systems enforce unique constraints through built-in constraint mechanisms.
Check Constraints
Check constraints enforce more complex business rules by restricting the values allowed in a column or a combination of columns. These constraints can involve multiple columns and complex logical expressions. For instance, a constraint might ensure that the value in a “quantity” column is always greater than zero or that the sum of values in multiple columns equals a specific value. Violating a check constraint will result in an error preventing the insertion or update of data that doesn’t satisfy the condition. Database systems support check constraints through declarative statements that specify the rule to be enforced.
| Constraint Name | Description | Impact of Violation | Enforcement Mechanism |
|---|---|---|---|
| Entity Integrity | Uniqueness and non-NULL values in primary keys. | Data redundancy, inconsistencies, difficulty in data retrieval. | Database constraints, triggers. |
| Referential Integrity | Foreign keys referencing valid primary keys. | Orphaned records, data inconsistencies. | Database constraints, cascading actions. |
| Domain Integrity | Values adhering to predefined data types and ranges. | Data corruption, inaccurate reporting. | Data type definitions, input validation. |
| Unique Constraints | Uniqueness of values in a column or set of columns. | Duplicate entries, data inconsistencies. | Database constraints. |
| Check Constraints | Enforcing complex business rules on column values. | Data that violates business rules, potentially leading to incorrect calculations or decisions. | Database constraints. |
Implementing Business Critical Integrity Constraints
Implementing business critical integrity constraints is crucial for maintaining data accuracy, consistency, and reliability within a database system. This process involves defining and enforcing rules that prevent invalid or inconsistent data from entering the system. Effective implementation ensures data integrity, protects against errors, and facilitates accurate reporting and decision-making.
Referential Integrity Constraint Implementation
Referential integrity ensures that relationships between tables are correctly maintained. This is typically achieved through foreign key constraints. The process involves specifying a foreign key column in one table that references a primary key column in another table. This constraint prevents the insertion or update of data that violates the defined relationship. For example, consider an `Orders` table with a `CustomerID` foreign key referencing the `Customers` table’s `CustomerID` primary key. Attempting to insert an order with a `CustomerID` that doesn’t exist in the `Customers` table would be prevented by the referential integrity constraint. Database systems provide mechanisms, often through SQL commands like `ALTER TABLE`, to define and enforce these constraints. The specific syntax varies slightly depending on the database system (e.g., MySQL, PostgreSQL, SQL Server).
Check Constraint Enforcement
Check constraints are used to validate data against predefined business rules. These rules can be simple comparisons (e.g., ensuring a value is positive) or complex logical expressions. To enforce a check constraint, the database system verifies that the condition specified in the constraint is met before allowing data modification. For example, a check constraint on an `Age` column could ensure that all values are greater than or equal to zero and less than 120: CHECK (Age >= 0 AND Age < 120). This constraint prevents the insertion or update of invalid age values. The implementation involves defining the check constraint as part of the table's schema using appropriate SQL commands.
Unique Constraint Creation
Unique constraints ensure that all values in a specified column or set of columns are unique within a table. This prevents duplicate entries and maintains data consistency. Creating a unique constraint involves specifying the column(s) that must be unique using SQL commands. For example, an email address in a `Customers` table should be unique. A unique constraint on the `Email` column would prevent the addition of a customer with an email address already present in the table. The database system enforces this constraint by preventing the insertion or update of duplicate values.
Domain Constraint Implementation
Domain constraints restrict the values allowed for a particular column to a predefined set of values. This is similar to check constraints but offers a higher level of abstraction. Implementation involves defining a domain (a named set of allowed values) and then associating that domain with a column. For example, a domain named `OrderStatus` could be defined to contain values like 'Pending', 'Processing', 'Shipped', 'Delivered'. A column in the `Orders` table could then be defined to use this domain, ensuring that only these valid order statuses are permitted. The exact implementation methods vary across different database systems but generally involve creating a domain object and then referencing it when defining the table's columns.
Consequences of Violating Business Critical Integrity Constraints
Ignoring or failing to enforce business critical integrity constraints can lead to significant and far-reaching negative consequences, impacting data accuracy, operational efficiency, and ultimately, the financial health and reputation of an organization. The ramifications extend beyond simple data errors; they can trigger cascading failures, erode trust, and even lead to legal repercussions.
The potential consequences of failing to enforce these constraints are multifaceted and severe. Data inconsistencies and errors are the most immediate and obvious results. Inaccurate or incomplete data renders business processes unreliable, leading to flawed decision-making and potentially costly mistakes. For example, incorrect inventory data can result in lost sales due to stockouts or unnecessary expenses from overstocking. Similarly, inaccurate customer data can lead to failed deliveries, billing errors, and damaged customer relationships.
Financial Risks Associated with Integrity Constraint Violations
Violations of business critical integrity constraints directly translate into financial risks. These risks can manifest in several ways, including direct financial losses due to inaccurate transactions, increased operational costs associated with data correction and remediation, and potential legal penalties for non-compliance with regulations (such as GDPR or HIPAA). For instance, a bank failing to enforce constraints ensuring unique account numbers could lead to duplicate accounts, fraudulent transactions, and significant financial losses. The cost of rectifying such errors, including audits and legal fees, can be substantial. Furthermore, reputational damage resulting from such incidents can lead to decreased customer trust and loss of business.
Reputational Risks Associated with Integrity Constraint Violations
Data breaches and system failures stemming from neglected integrity constraints severely damage an organization's reputation. Loss of customer trust, diminished brand value, and negative media coverage can have long-lasting and devastating effects on the bottom line. For example, a healthcare provider failing to enforce constraints on patient data privacy could result in a major data breach, leading to significant fines, legal action, and irreparable damage to public confidence. The resulting loss of patients and subsequent decline in revenue can be catastrophic.
Examples of Real-World Data Breaches or System Failures
The 2017 Equifax data breach, which exposed the personal information of millions of consumers, is a prime example of the consequences of inadequate data integrity controls. The breach, attributed in part to vulnerabilities in their systems and a failure to patch known security flaws, resulted in significant financial losses, legal settlements, and lasting reputational damage. Similarly, numerous instances of financial institutions suffering from data breaches or system failures highlight the importance of robust integrity constraints. These failures often stem from a lack of proper validation and enforcement of critical data constraints.
Best Practices for Preventing Violations of Business Critical Integrity Constraints
Preventing violations requires a proactive and multi-faceted approach. It's crucial to establish a robust framework that combines technical safeguards with strong organizational policies and procedures.
The following best practices are essential for mitigating the risks associated with integrity constraint violations:
- Implement robust data validation rules: Enforce data integrity at the point of entry, preventing invalid data from entering the system in the first place. This includes using appropriate data types, input masks, and validation checks.
- Regularly audit and monitor data integrity: Conduct periodic audits to identify and address potential integrity violations. Implement monitoring tools to detect anomalies and potential breaches in real-time.
- Develop and enforce strict data governance policies: Establish clear policies and procedures for data handling, access control, and modification. These policies should Artikel responsibilities and accountability for maintaining data integrity.
- Invest in comprehensive security measures: Protect data from unauthorized access and modification through robust security measures, including firewalls, intrusion detection systems, and encryption.
- Provide comprehensive training to employees: Educate employees on the importance of data integrity and the procedures for handling sensitive data. This training should cover data validation, error handling, and security best practices.
- Utilize database normalization techniques: Properly normalize database schemas to minimize data redundancy and ensure data consistency.
- Employ version control and rollback capabilities: Implement mechanisms for tracking data changes and reverting to previous versions in case of errors or breaches.
Maintaining Data Integrity Over Time
Maintaining the integrity of business-critical data requires a proactive approach that anticipates and adapts to evolving business needs and technological changes. Ignoring this aspect can lead to inconsistencies, inaccuracies, and ultimately, compromised decision-making. A robust strategy for long-term data integrity encompasses managing changes to business rules, implementing effective monitoring and auditing procedures, establishing protocols for temporary constraint relaxation, and mitigating risks associated with data migration.
Managing Changes to Business Rules and Their Impact on Integrity Constraints
Changes in business rules necessitate corresponding adjustments to integrity constraints to maintain data accuracy and consistency. This process should be carefully managed to minimize disruptions and ensure the ongoing validity of the data. A change management process, including impact analysis, testing, and phased rollout, is crucial. For instance, if a company changes its customer segmentation criteria, the integrity constraints related to customer data (e.g., ensuring consistent categorization) must be updated accordingly. Failure to do so could lead to inaccurate reporting and flawed business decisions based on outdated segmentation. This process should involve close collaboration between business analysts, database administrators, and developers to ensure a smooth and effective transition.
Monitoring and Auditing Integrity Constraint Enforcement
Regular monitoring and auditing are essential for verifying the ongoing effectiveness of integrity constraints. This involves tracking constraint violations, analyzing their causes, and implementing corrective actions. Automated tools can play a vital role in this process, providing real-time alerts and generating reports on constraint compliance. For example, a system might monitor for violations of a unique constraint on customer IDs, alerting administrators to potential data duplication issues. Regular audits, both automated and manual, should be conducted to identify potential weaknesses in the system's integrity mechanisms and to ensure that the constraints are correctly enforced. These audits should be documented and reviewed regularly to identify trends and areas for improvement.
Handling Temporary Relaxation of Integrity Constraints
Situations may arise where temporary relaxation of integrity constraints is necessary, such as during data migration or system maintenance. However, this should be carefully controlled and documented. A formal request and approval process, including clear justification and defined timeframes, should be implemented. For example, a temporary relaxation of a foreign key constraint might be needed during a database upgrade to allow for temporary inconsistencies. Crucially, a rollback plan should be in place to restore the constraints and ensure data consistency once the temporary relaxation is no longer needed. This plan should include rigorous data validation to verify the integrity of the data after the constraints are re-enabled.
Mitigating Risks Related to Data Migration and Integrity Constraint Maintenance
Data migration presents significant risks to data integrity, especially concerning the maintenance of integrity constraints. A thorough data mapping and validation process is critical before, during, and after migration. This involves verifying that data transformations preserve the meaning and integrity of the data and that constraints are correctly implemented in the target system. Consider using a phased migration approach, migrating data in smaller batches to allow for easier error detection and correction. Robust testing, including both unit and integration tests, should be performed to ensure that constraints are correctly enforced in the new system. Comprehensive documentation of the migration process, including any necessary adjustments to integrity constraints, is also crucial for future maintenance and troubleshooting.
Case Studies of Business Critical Integrity Constraints

Understanding the practical implications of business critical integrity constraints requires examining real-world scenarios. This section presents two case studies: one showcasing successful implementation and the other highlighting the detrimental effects of failure. Analyzing these contrasting examples underscores the vital role these constraints play in maintaining data accuracy and business stability.
Successful Implementation: Maintaining Inventory Accuracy at a Pharmaceutical Distributor
Pharmaceutical distributors operate under stringent regulatory requirements demanding precise inventory tracking. One major distributor implemented a business critical integrity constraint ensuring that the quantity of medication in their database always matched the physical inventory count. This was achieved through a combination of barcode scanning at every stage of the supply chain, automated inventory updates integrated with their warehouse management system, and rigorous reconciliation processes. The constraint prevented discrepancies between recorded and actual stock levels, thereby avoiding potential stockouts, expired medication disposal, and regulatory non-compliance. The system also included automated alerts for any significant discrepancies, triggering immediate investigation and correction. This proactive approach minimized losses and ensured consistent compliance.
Negative Consequences: A Banking System's Failure to Enforce Transactional Integrity
A regional bank experienced significant financial losses due to a failure to implement a crucial integrity constraint in their online banking system. The constraint, designed to prevent duplicate transactions, was inadequately implemented. A software bug allowed duplicate transactions to be processed, leading to overdraft situations and incorrect account balances. This resulted in significant customer dissatisfaction, reputational damage, and substantial financial losses in resolving the discrepancies and compensating affected customers. The lack of a robust constraint also hampered their ability to accurately track and reconcile transactions, further complicating the situation. The incident resulted in a major system overhaul and significant investment in improving their data integrity controls.
Comparison of Case Studies, Which of the following is a business critical integrity constraint
The contrasting outcomes highlight the critical importance of robustly implementing business critical integrity constraints. The pharmaceutical distributor's success stemmed from a proactive approach, combining technological solutions with rigorous processes. Conversely, the bank's failure underscores the severe consequences of neglecting such constraints. A seemingly minor oversight in the banking system resulted in substantial financial and reputational damage. The difference lies in the prioritization of data integrity and the investment in robust systems and processes to maintain it.
| Case Study | Outcome | Lessons Learned |
|---|---|---|
| Pharmaceutical Distributor Inventory Management | Successful implementation prevented stockouts, minimized expired medication disposal, and ensured regulatory compliance. | Proactive implementation of constraints, combined with technological solutions and rigorous processes, is crucial for success. |
| Regional Bank Online Banking System | Failure to implement a duplicate transaction constraint resulted in significant financial losses, customer dissatisfaction, and reputational damage. | Neglecting business critical integrity constraints can lead to severe financial and reputational consequences. Robust testing and comprehensive implementation are vital. |